Im many parts of America, you wouldn’t leave your front door unlocked at night. You also wouldn’t leave your keys in your car in the driveway, either. This is why it is such a shame to see the things I do as an IT Professional. You see, I see people taking little or no precaution in guarding data that leaves their identities at risk.
No, this isn’t a paid advertising post for some company like the ones you hear about on talk radio. I just want you to think through some of the ways you do (or don’t) protect your data.
Identity Protection is about more than passwords. My day job is at an IT company. We handle everything from Enterprise Servers to home PC and Mac users. Good passwords are important, but a little common sense is necessary. About once a week, I get a machine in where I can tell the end user what happened before they even have to tell me the story. It kind of goes like this…
End User: ” I can’t get into windows” – “its locked with a password I don’t have”…
Me: They claimed they were from Microsoft and that they could see you had viruses, right?
End User: “How did you know?!”
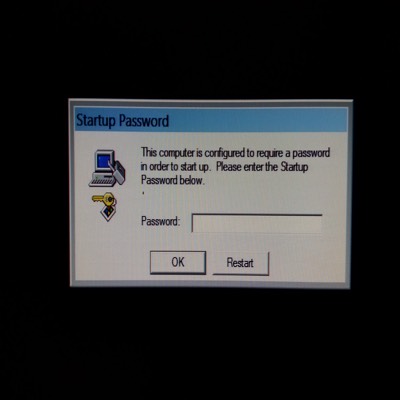
This is becoming a pretty common way to get someone’s information via a little social engineering. You see, criminals don’t have to expend energy to try and guess password information or credit if they can convince people to willingly give it. The flavor of the scam this month is to tell people they are from Microsoft and they have detected viruses on your computer. They step you through giving them remote access to your computer, and then they run fake virus scans that “prove their point”. In some cases, they actually infect your computer with viruses and malware. There have also been cases where, during the “remote service call” the “customer” refuses to pay or give credit card info, and the criminal uses a utility in Windows called syskey to lock the computer with a passcode before Windows will boot. It also encrypts part of the Windows registry. At that point, your best option is to have your hard drive attached to another machine with a working copy of Windows, so you can remove your data. You then will have to have the drive formatted and Windows reloaded.
So let’s review. Protect your credit card information. Never let a third party that calls you out of the blue access your computer, no matter who they claim to be.